Cyberwarfare is in the news these days because of the Russian hacking of the DNC. It has been suggested that perhaps the U.S. could foil a launch of missiles by North Korea through cyberattacks on the computers in their launch systems. The possibility of cyberattacks on U.S. military systems have not received a great deal of coverage in the media but they are a very real and dangerous threat.
In the 1990s, a breach in a firewall protecting an important U.S. Naval radio transmitter in Maine could have allowed hackers to transmit control codes to ballistic missiles aboard U.S. submarines. This problem was so serious that after the breach was fixed, the U.S. Navy changed its procedures for submarine missile launch to require any unexpected launch commands to be verified by a second source before triggering missile launches.
In 2010, fifty Minuteman missiles disappeared from their control computer monitors for over an hour. The missiles crews worked frantically to find out what was wrong. There was a fear that an enemy had taken control of the missiles and could prevent them from being launched or, even worse, could launch them at unknown targets. It turned out that a circuit board had been installed incorrectly and the problem was fixed.
After the Minuteman missile the incident, President Obama ordered an inspection of missile control systems to find out if there were other potential problems. One of the problems discovered involved internet connections to the Minuteman missile silos. There was a gap in security that could have allowed hostile agents to shut down the missile guidance systems. The damage that could have been caused would have taken weeks to repair.
These problems raise the prospect of a country being able to cause the missiles of a second country to be launched against a third country. In the age of hair-trigger missiles which are ready to launch in minutes, a major retaliation against an innocent country could be over before anyone knew that country's missiles control systems had been hacked. Another grave possibility is that hackers could cause warning systems to falsely report a launch of missiles by an adversary that would invite a retaliation before any such hacking could be discovered and reported.
The U.S. purchases components for nuclear missile systems from a variety of commercial sources. These components could be infected with malware such as viruses, trojans and/or worms. Some of the components on the market are manufactured in countries that could be opponents in future military confrontations. It would only be wise for such countries to build backdoors into their components that would let them remotely sabotage them or shut them off in a conflict.
If there were enemy agents within our defense establishment, they could exacerbate cyberattacks by sabotage or by deliberately inserting malware or opening links to enemy computers. Currently, postings to Minuteman missile silos are very unpopular which would make it easier for enemy infiltration. Much more needs to be done to tighten security for U.S. nuclear missile systems.
It would be best for us and the Russians to take our missiles off of their current hair-trigger launch status that only give decision makers minutes to decide if a launch warning is valid and to order retaliation. Better monitoring and control should be developed over the supply chain of components for nuclear missile systems. Better ways to protecting the miles of wiring and the computers in our missile launch systems need to be developed. And, finally, the widespread practice of cyberintrusion into the military computer systems of all countries should be outlawed by international treaty to reduce the risk of nuclear war.
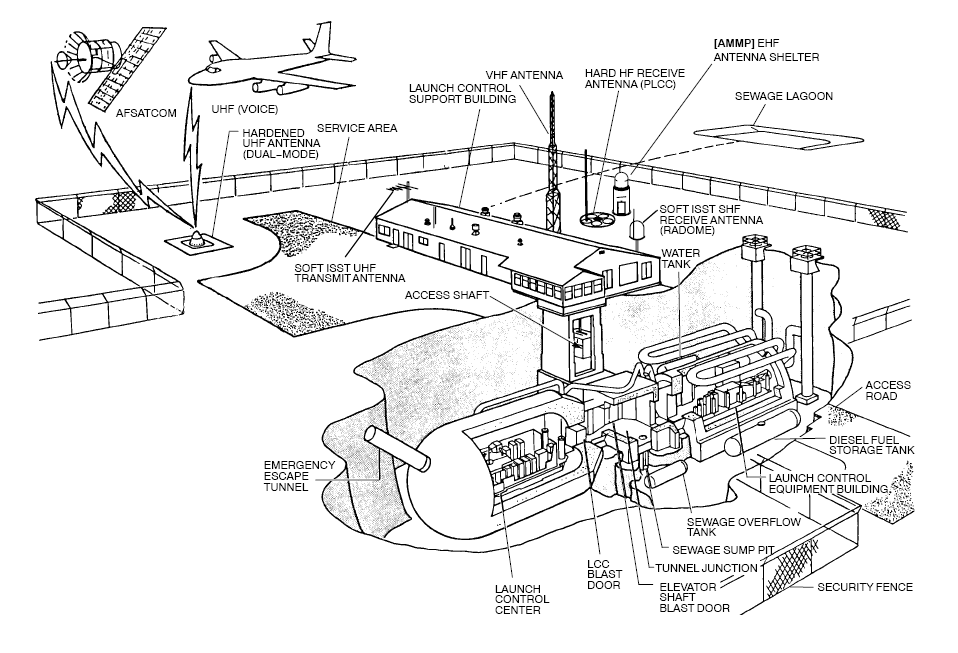
Minuteman missile control bunker: